|
Our monitoring systems run on cloud servers in multiple hosting facilities [the rectangle in the diagram represents one facility].
External monitoring
First, we look at each monitored site from the viewpoint of the “visitor” or browser. We select URLs for pages, javascript and other resources that are typically compromised in an attack. The URLs may be assigned to different monitors in different physical facilities.
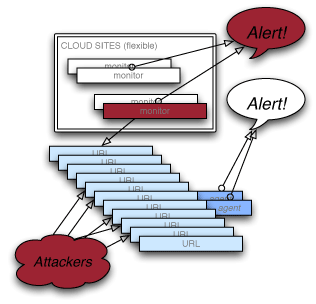
When an attack takes place, the characteristics of these pages or files change— newly-injected javascript or iframes may appear, among other things. Our monitors detect deviations from the “normal” state and immediately notify webmasters and security personnel by email or SMS.
We also check the pages against the Google Safe Browsing database which monitors for malware distribution sites. If GSB reports there’s malware on the site we’re monitoring, or any site it connects to (several levels deep), we send a notification.
| |
The monitoring systems are tightly secured and unlikely to be compromised because they expose nothing to the outside world. In the event one of them fails, another takes over. Monitoring of any given URL may shift from one physical facility to another over time, and new monitors (that hackers cannot discover) sit quietly waiting for deployment.
Internal monitoring
For many server configurations there are additional tools we can put in place. These software tools are installed on the servers themselves. They examine the site, or database, or other service, from the “inside” rather than the outside, watching for telltale signs of compromise.
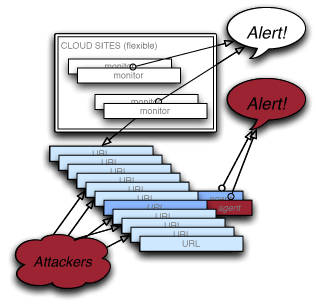
If a system is breached, these smart agents can detect it rapidly, and we can then send alerts to your security team. These agents are still passive, in the sense that they do not open up any communications with the outside world — they only report back when they’re asked how they’re doing.
|
